Securing the global supply chain, while ensuring its smooth functioning, is essential to our national security and economic prosperity. This vital system provides the goods that feed our domestic critical infrastructures.
The global supply chain is dynamic, growing in size and complexity, and is vulnerable to threats and hazards such as natural disasters, accidents or even malicious attacks. A common approach, involving the range of stakeholders with supply chain roles and responsibilities, is necessary.
To ensure an effective Supply Chain Security, there are seven key strategies in place.
Figure 1: Various Mode of Transport for Global Supply Chain

Table of Contents
Container & Seal Security and Inspection
All international supply chain business partners must ensure procedures are in place to maintain container integrity. Container integrity is maintained to protect against the unauthorised material and/or persons. Procedures must be in place to properly seal and maintain the integrity of shipping containers.
Procedures must be in place to verify the physical integrity of the container structure prior to loading/unloading and include the reliability of the locking mechanisms of the doors.
The following seven-point inspection process is recommended:
1. Check the front wall for integrity or manipulation
2. Check the left side for integrity or manipulation
3. Check the right side for integrity or manipulation
4. Check the floor for integrity or manipulation
5. Check the ceiling/roof for integrity or manipulation
6. Check the doors (both inside and outside) for integrity or manipulation
7. Check the outside undercarriage for integrity or manipulation
A trailer/container inspection checklist should be used to ensure that all items have been checked
Written procedures must stipulate how seals are to be controlled and affixed to loaded containers. Procedures must be in place for reporting compromised seals and/or containers. Only designated employees should have access to the security seals and distribution of container seals (container sealing).
Figure 2: Seven Point Inspection Process

Personnel Security
a. Conducting Comprehensive Investigations
Before hiring an employee, an in-depth criminal and background investigation is conducted. These include checking criminal records, court records, financial history, right to work documents, past employment and education records.
b. Background Checks for Employees
All employees are subject to background investigations. This is to ensure the integrity of persons having access to its facility and assets.
c. Utilising Biometric Technology
Using biometric handprint identification system together with a 4-digit employee code to access work area and authenticate identities.
d. Monitoring Access Patterns
Periodically reviews proximity reader system to identify unusual patterns of employee access.
e. Terminating Facility Access
When an employee is terminated, an information notice should be issued to workers. A list of names and photos of terminated employees should be given to security to aid them in access control of the facility.
f. Restricting Access
Proximity cards with photo identification should be used to gain access to different areas based on their job function. Entry and exit times should be restricted according to work schedule.
g. Requiring Employee Identification
All employees should wear their photo identification badge for verification.
Figure 3: Various Security Devices

Secured Procedures
A layered approach is the best way to secured procedures. The right combination of planning, processes, contract, packaging, and monitoring helps ensure goods reach their intended destinations.
Measures to boost security may include expedited service, dedicated trucks, team drivers, covert and overt GPS, split shipments, couriers, auditing partners, and careful timing, such as avoiding shipping during weekends and holidays.
Designing a secure goods supply chain starts with mapping the supply chain to identify risk areas. Next comes assessing processes, assets and facilities throughout the entire network, including logistics providers and suppliers.
Then security managers can recommend tools that will best mitigate the risks. Monitoring and measuring security procedures is important to ensure successful results.
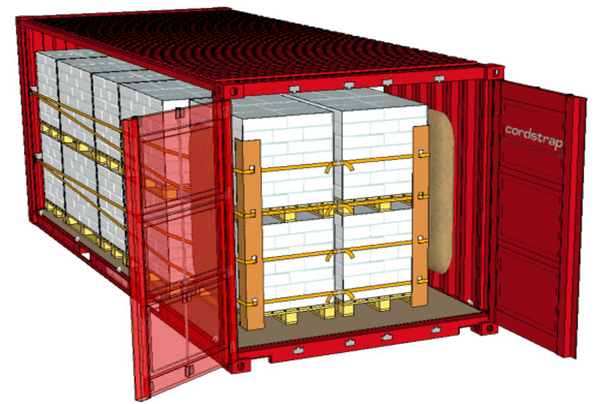
One key process is making sure goods are properly prepared for transit. Seagate, for example, uses corner boards, strapping, banding, and shrink wrapping to protect its products in transit.
Figure 4: Secured Cargo in Container
Documentation Control
Documentation is important for physical logistics operations, the financial, trading and accounting processes of the both buyer and seller organisations and partner
It is depended upon the entire set of documentation pertaining to each transaction to be able to recognise the sale, recognise value of consignment and effect necessary payment.
All documents should be legible and accurate. Outgoing and incoming cargo must be verified against purchase and delivery orders
Accounting practices require detailed documentation.
Finally, goods and services are recognised and identified only with the set of authenticated documentation showing ownership based on which the customs allow them to be exported or imported.
There are more aspects like terms of carriage by the carrier coupled with insurance liabilities and coverage that call for set of documentation covering specific aspects of each transaction.
The entire set of documents and the terms of trade have been developed and standardised across all countries to facilitate international trade.
A supply chain manager needs to be aware of the complete set of documentation requirement along with the various aspects to be able to design processes and documentation control mechanisms.
Errors in documentation will lead to financial damage, delays in delivery and performance.
Figure 5: A person using computer for documentation from various places

Facility Security
Caged area that encloses the top and side of the truck in order to restrict access to the truck during loading. The caged area should be locked when not in use.
Signs posted stating “Restricted Access” should be visible
• Utilising Technology to monitor gates
Facilities should have electronic gates, perimeter fences with infrared and magnetic sensors, motion detectors and alarms.
• Selecting Contracted Security Guard Services
A comprehensive plan should be in place. This plan includes evaluating the service provider’s selection, training and supervision of the guards.
• Lighting
Immediately replace lights that burn out. Conduct survey of facility’s interior and exterior lighting to ensure uniformity and appropriate brightness.
The full content is only visible to SIPMM members
Already a member? Please Login to continue reading.
References
Alvin Tan (2017), “Key Strategies to implement a Digital Supply Chain”. Retrieved from https://publication.sipmm.edu.sg/key-strategies-implement-digital-supply-chain, accessed 16/03/2018.
Boeing Suppliers (2018). “International Container Security”. Retrieved from:
http://www.boeingsuppliers.com, accessed 16/03/2018.
BSI (2018). “Security Training and Threat Awareness in the Supply Chain”. Retrieved from: https://bsi.learncentral.com, accessed 16/03/2018.
C-TPAT (2006). “Supply Chain Security Best Practices Catalog”. Retrieved from: https://www.cbp.gov, accessed 16/03/2018.
Customs Cleared Company Inc. (2012). “Trailer/Container Security”. Retrieved from: http://www.customscleared.com, accessed 16/03/2018.
Lisa Terry (2014). “Protecting High-Value Cargo: A Sense of Security”. Retrieved from: http://www.inboundlogistics.com, accessed 16/03/2018.
National Cyber Security Centre (2018). “Supply Chain Security Collection”. Retrieved from: https://www.ncsc.gov.uk, accessed 16/03/2018.
Prachi Juneja (2018). “Documentation – A Control Mechanism of Supply Chain Logistics”.
Retrieved from: https://www.managementstudyguide.com, accessed 16/03/2018.
Raghavendran, A. (2013). “Eight Keys to Global Supply Chain Security”. Retrieved from: http://www.mhlnews.com, accessed 16/03/2018.
US Department of Homeland Security (2017). “National Strategy for Global Supply Chain Security”. Retrieved from: https://www.dhs.gov, accessed 16/03/2018.





