Modern procurement processes integrate several technologies to better process internal business operations. Organizations are rapidly using automated procurement management tools, whether using enterprise resource planning (ERP) or less advanced tools.
As more e-procurement tools are introduced to the IT stack of a business, the role of cybersecurity in the procurement process becomes crucial to protect sensitive corporate data and minimize the risks inherent in an ever-growing supply.
Table of Contents
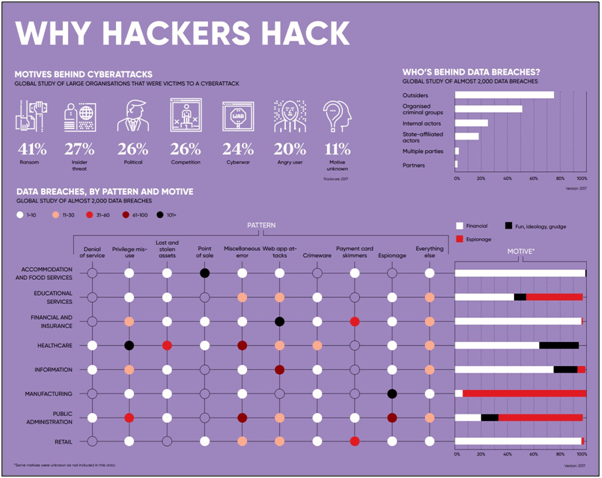
Motives Behind Cyber Attacks
Misuse of employee rights and non-compliance with cybersecurity policies are the most common problems. Company devices are sometimes used for non-work purposes, or for work, but in unsecured areas. Via phishing scams, inefficiently trained or careless workers may then be unwittingly lured into downloading malicious third-party software on the company’s computer, with malware soon spreading across the network of the organization. Either by direct stealing or by encrypting confidential data and keeping it for ransom, the purpose of an attack can be financial gain, or it can be to achieve a non-financial objective, such as harming the reputation of an entity or government.
For the sheer excitement of it, or for a sense of accomplishment, some hackers also enjoy taking down computer systems. In any case, recognizing that the entire supply chain is susceptible to attack at any time is critical for organizations.
Three Layers of Mitigation
There are 3 main components in cybersecurity risk mitigation:
- Threat prevention: Deter threat actors from threatening enterprise. applications and data by employing best practices and strategies
- Identification of risks: Security instruments and management to classify active security threats.
- Threat remedy: Utilizing techniques and instruments to reduce the effect of active security threats by isolating or containing the threat that have gotten past corporate security defences and penetrated the network.

Cybersecurity Solutions
It is crucial for companies to have the technologies that are efficient enough to deliver well-updated security controls and processes, to address procurement cybersecurity in the most effective way. Having these controls and implementing them is the first step in establishing an effective cybersecurity framework.

Types of cybersecurity solutions include:
- Security patch management schedule
While “zero-day” attacks are feared by companies, many successful attacks are accomplished using known exploits. Therefore, attacks on network infrastructure can be prevented by maintaining a strict schedule for patch/update management.

- Intrusion Detection Systems (IDS)
IDS may not stop an attack; however, they are critical technology for logging intrusion attacks, and to alert response team of breach occurrence. By utilising IDS, cybersecurity breaches can be studied to check how attackers are able to enter the system, what they have done, and data accessed. Doing so will help to develop measures to avoid future attempts.
- Managed cybersecurity services/solutions
Cybersecurity can be outsourced to IT solutions providers. They will be able to assess and audit companies’ internal and external security susceptibilities. They will have a team of IT security experts and help to develop and implement a cybersecurity solution.
- Multi-layered firewalls
Defence-in-depth strategy will use multiple layers of defence to slow the attacked down as much as possible until their access can be cut off. All the different resources in the companies’ network can be isolated from one another by utilising multiple layers of defence. “Per-app” firewalls can filter traffic requests for every application the business runs. The more layers of security that an attacker must go through to access the companies’ resources, the more chances you have to identify and stop them.

Suppliers Assessment
Suppliers’ websites might be used by cybercriminals to host malware, so it is always a good practice to check on the suppliers and evaluate their security parameters. To mitigate the possibility of such attacks, organizations should require suppliers to adhere to processes and protocols. The suppliers’ security parameters should be checked at regular intervals. Risk management programs can be established with security policies to evaluate suppliers and work with them to execute the plans. Expertise can be provided by the IT department to help suppliers with the technical know-how. Control gates can be established to ensure risks are managed throughout the suppliers’ lifecycle (sourcing, onboarding, execution, and off-boarding). There can be in the form of due-diligence check, periodic assessments/audits, or insertion of full cybersecurity program.

Employee Education
Investments in employee training and education on procurement cybersecurity should be one of the top priorities of organizations. Employees must be watchful and not fall in the traps of cybercriminals and allow them to enter companies’ network to extract sensitive data. Regular circulars should inform employees of cybersecurity issues affecting the organizations, this way they will know how to identify risks. Organizations should create and regularly review incident response plan, while ensuring full and proper compliance within the team.
The full content is only visible to SIPMM members
Already a member? Please Login to continue reading.
References
Center for Internet Security. (2020). “EI-ISAC Cybersecurity Spotlight – Backups”. Retrieved from https://www.cisecurity.org/spotlight/ei-isac-cybersecurity-spotlight-backups/#:~:text=What%20it%20is,for%20data%20protection%20and%20recovery, accessed 08/12/2020.
Christophe Blassiau and Danial Bartel. (2020). “Solidifying Trust in the Digital Ecosystem”. Retrieved from https://blog.se.com/energy-management-energy-efficiency/2020/10/21/solidifying-trust-in-the-digital-ecosystem/, accessed 08/12/2020.
Claire Kirk. (2019). “Here’s How to Develop a Cybersecurity Recovery Plan”. Retrieved from https://www.lightedge.com/blog/develop-a-cybersecurity-recovery-plan/, accessed 08/12/2020.
David Toh Rongli, ADPSM. (2019). “Six Crucial Factors on Cyber Security for Healthcare Procurement”. Retrieved from https://publication.sipmm.edu.sg/six-crucial-factors-cyber-security-healthcare-procurement/, accessed 08/12/2020.
Eric Dosal. (2018). “ Top 4 Cybersecurity Solutions for Your Company to Use Now!”. Retrieved from https://www.compuquip.com/blog/top-4-cybersecurity-solutions-for-your-company-to-use-now, accessed 08/12/2020.
Forrest Stroud. (2020). “Cyber Security Threat Mitigation”. Retrieved from https://www.webopedia.com/TERM/C/cyber-security-threat-mitigation.html#:~:text=Cyber%20security%20threat%20mitigation%20refers,when%20security%20attacks%20do%20happen, accessed 08/12/2020.
Ginna Koo, GDSCM. (2017). “Digital Procurement for Effective Supply Chain Management”. Retrieved from https://publication.sipmm.edu.sg/digital-procurement-for-effective-supply-chain-management/, accessed 08/12/2020.
Jeff Aldorisio. (2020). “Whats’s the Role of Cybersecurity in Procurement?”. Retrieved from https://securityscorecard.com/blog/role-of-cybersecurity-in-procurement, accessed 08/12/2020.
Mehr Bhalla. (2018). “7 Ways to Strengthen Procurement Cybersecurity in 2019”. Retrieved from https://www.zycus.com/blog/procurement-technology/procurement-cybersecurity-2019.html, accessed 08/12/2020.
WBR Insights. (2020). “Here’s How the Procurement Industry Can Understand and Meet the Challenges of Cybersecurity”. Retrieved from https://procureconwest.wbresearch.com/blog/heres-how-the-procurement-industry-can-understand-and-meet-the-challenges-of-cybersecurity, accessed 08/12/2020.

